The Fourth Industrial Revolution, defined by the convergence of emergent technologies that blur the lines of the physical, digital, and biological spheres, comes with its own challenges. Cyberespionage is one of them.
As the world becomes more interconnected, it is important to be aware of how different nation-state actors can utilize this connectivity to advance various geopolitical agendas. In its recently concluded ESET World 2021 web forum, security solutions firm ESET discussed how cyberespionage has been evolving through the years and targeting the African region in three distinct campaigns that occurred in the past year.
The first case involves the cybercrime group Lazarus. ESET researchers have discovered a previously undocumented Lazarus backdoor, which they have dubbed Vyveva, being used to attack a freight logistics company in South Africa.
The backdoor consists of multiple components and communicates with its C&C server via the Tor network. ESET researchers have found its installer, loader and main payload – a backdoor with a TorSocket DLL. The previously unknown attack was discovered in June 2020.
“Although Vyveva has been used since at least December 2018, its initial compromise vector is still unknown. Our telemetry data suggests targeted deployment as we found only two victim machines, both of which are servers owned by a freight logistics company located in South Africa. The backdoor features capabilities for file exfiltration, timestomping, gathering information about the victim computer and its drives, and other common backdoor functionality such as running arbitrary code specified by the malware’s operators. This indicates that the intent of the operation is most likely espionage,” ESET explained.
The backdoor, Vyveva’s main component, connects to C&C servers and executes commands issued by the threat actors. It features 23 commands, some of which are asynchronous and executed in their own threads. Most of them are ordinary commands for file and process operations or information gathering, but there is also a less common command for file timestomping. It can copy creation/write/access time metadata from a “donor” file to a destination file or use a random date in the years 2000—2004.
“We see that the Lazarus Group evolves. It will target new people and will also use new tools. Usually the transportation vertical is not a sector that the group operates widely in. In this case, we saw a shift from their normal operations,” said Jean-Ian Boutin, head of threat research, ESET Canada Recherche.
The second case, involving the group TA410 which operates by utilizing LookBack and FlowCloud backdoors, targeted a diplomatic organization in West Africa.
“We’ve seen the infections sector going from spearphishing to targeting web-facing servers. State actors will always go for the weakest links of an organization. We’ve also seen a shift of vertical, going from the utilities sector to the diplomatic sector,” Mr. Boutin said.
“And this brings us back to the overarching theme, in which defenders should focus on Tactics, Techniques, and Procedures (TTPs) so that they can better protect their organization. As we’ve seen, groups will evolve, they will change their tactics, they will change their malware, and they will change which sectors and which regions of the world they are targeting.”
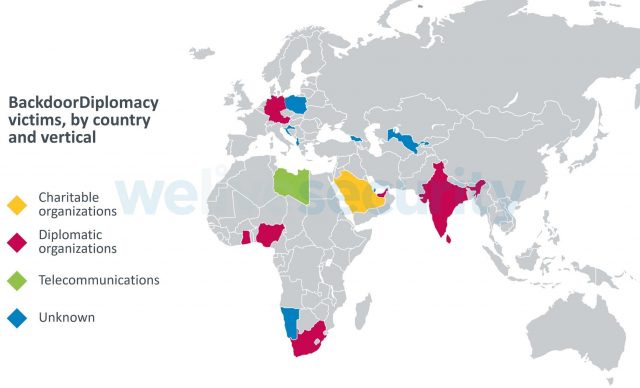
In the last campaign, ESET Research has uncovered a new APT (advanced persistent threat) group, dubbed BackdoorDiplomacy, that primarily targets Ministries of Foreign Affairs in the Middle East and Africa, and less frequently, telecommunication companies.
ESET found that their attacks usually start by exploiting vulnerable internet-exposed applications on webservers in order to install a custom backdoor that ESET is calling Turian. BackdoorDiplomacy can detect removable media, most likely USB flash drives, and copy their contents to the main drive’s recycle bin. The research was exclusively previewed at the annual ESET World conference this week.
“BackdoorDiplomacy shares tactics, techniques, and procedures with other Asia-based groups. Turian likely represents a next stage evolution of Quarian, the backdoor last observed in use in 2013 against diplomatic targets in Syria and the United States,” Mr. Boutin, who worked on this investigation along with Adam Burgher, senior threat intelligence analyst at ESET, said.
Turian’s network encryption protocol is nearly identical to the network encryption protocol used by Whitebird, a backdoor operated by Calypso, another Asia-based group. Whitebird was deployed within diplomatic organizations in Kazakhstan and Kyrgyzstan during the same timeframe as BackdoorDiplomacy (2017-2020).
Victims of BackdoorDiplomacy have been discovered in the Ministries of Foreign Affairs of several African countries, as well as in Europe, the Middle East, and Asia. Additional targets include telecommunications companies in Africa, and at least one Middle Eastern charity. In each case, operators employed similar tactics, techniques, and procedures (TTPs), but modified the tools used, even within close geographic regions, likely to make tracking the group more difficult.
BackdoorDiplomacy is also a cross-platform group targeting both Windows and Linux systems. The group targets servers with internet-exposed ports, likely exploiting poorly enforced file-upload security or unpatched vulnerabilities – in one instance leading to a webshell, called China Chopper, used by various groups. The operators attempted to disguise their backdoor droppers and evade detection.
A subset of victims was targeted with data collection executables that were designed to look for removable media (most likely USB flash drives). The implant routinely scans for such drives and, upon detecting insertion of removable media, attempts to copy all the files on them to a password-protected archive. BackdoorDiplomacy is capable of stealing the system information of the victim, taking screenshots, and writing, moving, or deleting files.
For more technical details about BackdoorDiplomacy, read the blogpost “BackdoorDiplomacy: Upgrading from Quarian to Turian” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.